x86进程线程
1、EPROCESS
进程结构,每个进程都有这样一个结构。EPROCESS中还有一个KPROCESS,其中EPROCESS被称为执行体,主要是给R3进行访问;KPROCESS才是真正的对象结构。
1 | //0x2c0 bytes (sizeof) |
Pcb:Kprocess结构体。内核成员,见下文。
ProcessLock:R3进程锁。修改EPROCESS结构存放锁结构,防止同时修改。改完了置0.
CreateTime:进程的创建时间。
ExitTime:进程的退出时间。
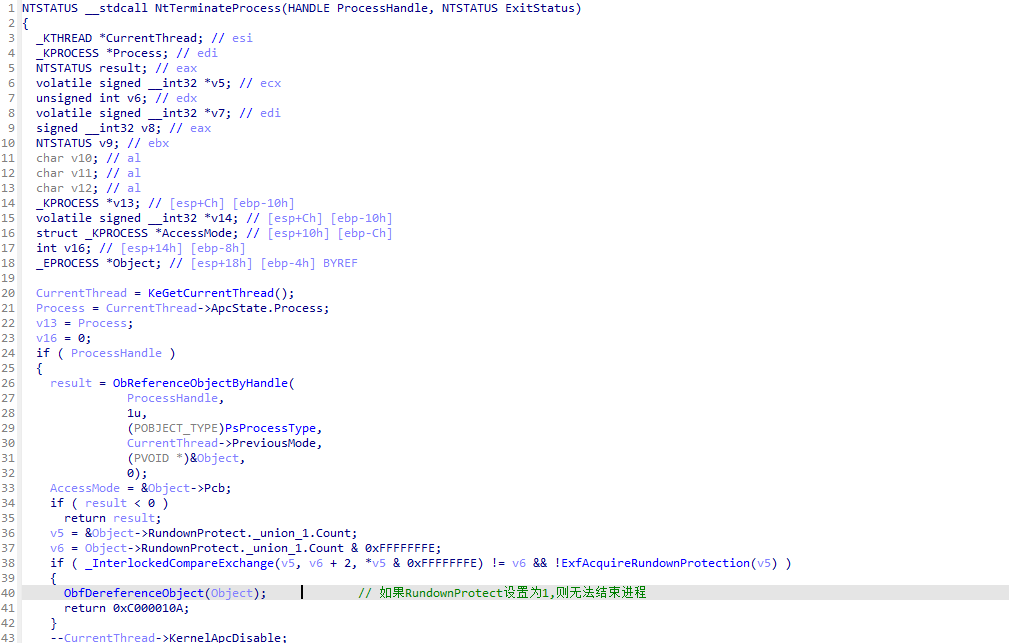
RundownProtect:进程锁。该字段置值后,进程无法被访问、打开、结束,相当于保护。但是会容易卡死。